How to Prevent Data Breaches in On-Demand Apps: Security Tactics That Work in 2025
In the fast-paced world of on-demand services, convenience is king. From ride-sharing and food delivery to freelance platforms and instant grocery services, these apps have seamlessly integrated into our daily lives. They offer unparalleled ease, connecting users with services in real-time. However, this very convenience, built on a foundation of constant data exchange and personalized interactions, makes on-demand applications a prime target for cybercriminals. As we navigate through 2025, data breaches are not just an unfortunate incident; they are a growing, existential threat to businesses. A single breach can erode user trust, incur crippling financial penalties, and severely damage a brand's reputation. The stakes are higher than ever, making robust on-demand app security a non-negotiable imperative.
This comprehensive guide is designed for app developers, CTOs, founders, and product managers alike. We’ll take a deep dive into the vulnerabilities inherent in these platforms and, more importantly, equip you with security tactics that work in 2025 to prevent data breaches and safeguard your business.
Why On-Demand Apps Are Highly Vulnerable
The very nature of on-demand apps, which thrive on dynamic interactions and vast user bases, creates unique security challenges:
- Real-time Data Exchange and Geo-tracking: On-demand apps continuously process sensitive real-time data, including user locations, payment details, and personal preferences. This constant flow of data between users, service providers, and platforms offers numerous interception points for attackers.
- Mobile-First Architecture: While mobile apps offer convenience, they also introduce specific vulnerabilities related to device security, network conditions, and user behavior.
- Dependence on Third-Party APIs: Most on-demand apps integrate with numerous third-party services (payment gateways, mapping services, communication tools). Each integration point can be a potential weak link if not properly secured, expanding the overall attack surface.
- Sensitive Personal Data at Scale: These platforms collect vast amounts of personally identifiable information (PII), including full names and addresses, payment card details, and even health information (in some specialized services). The sheer volume of this data makes it an incredibly attractive target for malicious actors.
- High Volume of User Activity (Attack Surface): Millions of daily transactions and user interactions mean more opportunities for cybercriminals to find and exploit vulnerabilities. This extensive "attack surface" necessitates constant vigilance.
The rising sophistication of cyber attacks on on-demand platforms underscores the need for proactive and adaptive defenses. Attackers are leveraging AI to automate phishing, bypass traditional security measures, and identify vulnerabilities faster than ever.
Top Security Tactics That Work in 2025
Preventing data breaches requires a multi-layered approach, addressing various attack vectors. Here are the core strategies you must implement:
a. Implement Strong Data Encryption in Apps
Encryption is the bedrock of data security. For on-demand apps handling sensitive information, robust encryption is paramount, both for data in transit and at rest.
- Data in Transit (Communication): All communication between the app, servers, and third-party APIs must be encrypted. TLS 1.3 (Transport Layer Security) is the current recommended standard, ensuring secure, authenticated, and encrypted channels. Avoid older, vulnerable versions like SSLv3 or TLS 1.0/1.1. HTTPS should be universally enforced.
- Data at Rest (Storage): Sensitive data stored on the user's device (e.g., temporary user profiles, cached payment tokens) or backend servers must be encrypted. AES-256 (Advanced Encryption Standard with 256-bit keys) remains the global standard for symmetric encryption, offering strong security and performance. For server-side databases, ensure full disk encryption and application-level encryption for sensitive fields. Key management – the secure generation, storage, rotation, and destruction of encryption keys – is as crucial as the encryption itself.
By prioritizing data encryption in apps, you minimize the impact if an unauthorized party gains access to your systems or intercepts communications.
b. Use Secure APIs for Mobile Apps
APIs (Application Programming Interfaces) are the backbone of on-demand apps, facilitating communication between different components and services. Insecure APIs are a major source of data breaches.
- Token-Based Authentication: Implement OAuth 2.0 and JWTs (JSON Web Tokens) for modern, secure, and stateless authentication. These tokens should have short lifespans and be regularly refreshed, reducing the window of opportunity for attackers if a token is compromised.
- Rate Limiting: Protect your APIs from brute-force attacks and denial-of-service (DoS) attempts by implementing strict rate limits. This prevents a single user or IP address from making an excessive number of requests in a short period.
- Encrypted Communication: As mentioned with general data encryption, all API calls must occur over HTTPS with modern TLS versions to prevent man-in-the-middle attacks.
- Encrypted Communication: Validate all incoming API requests rigorously against defined schemas (e.g., OpenAPI/Swagger). Reject any requests that deviate in type, length, or format to prevent injection attacks (like SQL injection or XSS) and unexpected data manipulation.
- API Gateway: Utilize an API Gateway to centralize security policies, authentication, authorization, rate limiting, and logging. This adds an essential layer of protection before requests reach your backend services.
Ensuring secure APIs for mobile apps is paramount, as they are often the primary entry points for data exchange.
c. Enforce Two-Factor Authentication (2FA)
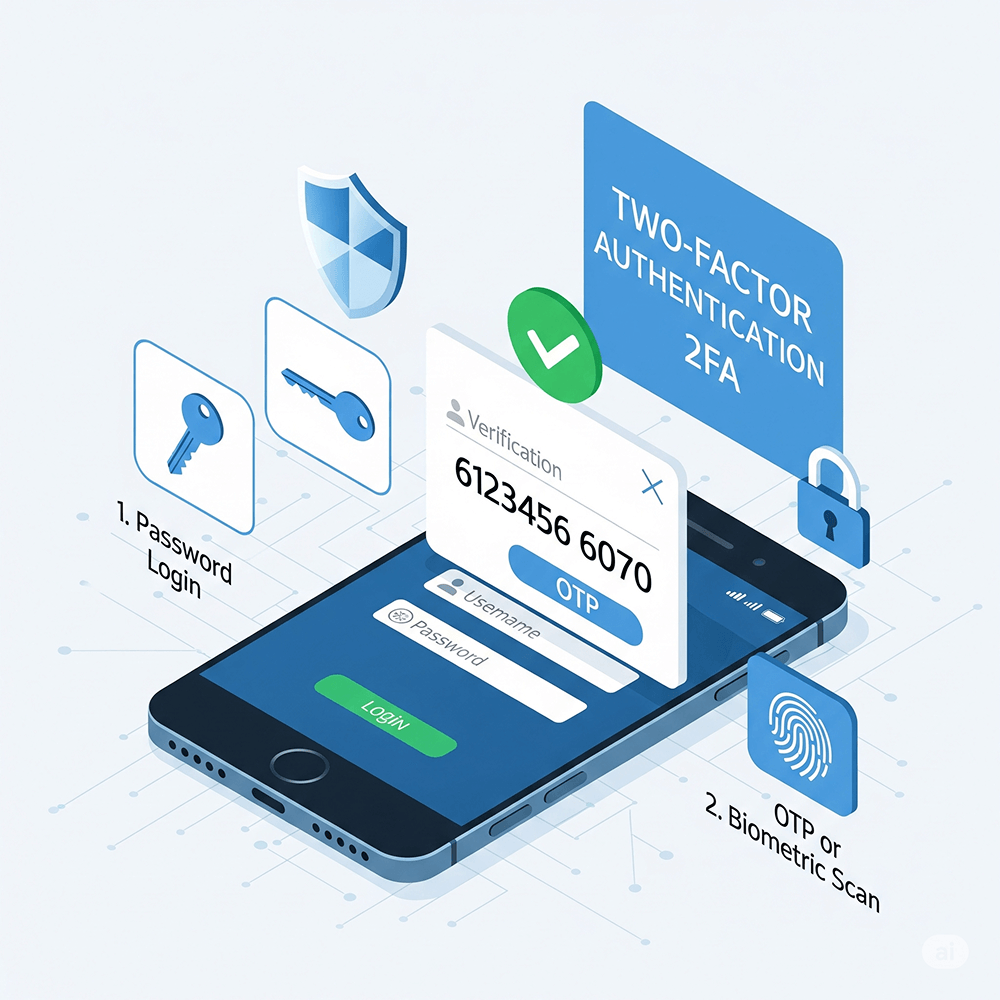
Even with strong passwords, compromised credentials remain a leading cause of data breaches. Two-factor authentication (2FA) adds a critical layer of security beyond just a password.
- For Users: Implement 2FA (or multi-factor authentication, MFA) for all user accounts, especially those with access to sensitive features or payment information. Common methods include SMS codes, authenticator apps (like Google Authenticator), or biometric verification (fingerprint, facial recognition). The rise of passwordless authentication using biometrics and FIDO2 standards is a significant trend in 2025, offering enhanced security and user convenience.
- For Admins/Developers: It is critical to enforce strong MFA for all internal accounts with access to app infrastructure, databases, and sensitive configuration settings. A compromised admin account can lead to catastrophic breaches.
By enforcing two-factor authentication, you significantly reduce the risk of unauthorized access even if primary user authentication methods are compromised.
d. Adopt Secure Coding Practices
Security isn't an afterthought; it must be ingrained into every stage of the software development lifecycle. Secure coding practices for apps are fundamental to building resilient on-demand platforms.
- Follow OWASP Mobile Top 10 Standards: The OWASP (Open Web Application Security Project) Mobile Top 10 provides a regularly updated list of the most critical security risks in mobile applications. Developers must be intimately familiar with these vulnerabilities (e.g., insecure data storage, insecure communication, improper authentication) and actively mitigate them. The 2025 OWASP Mobile Top 10 will highlight emerging threats and critical vulnerabilities relevant to today's mobile landscape.
- Input Validation: Beyond APIs, validate all user input at the application layer to prevent injection attacks.
- Error Handling: Implement robust error handling that avoids revealing sensitive system information or stack traces to potential attackers.
- Session Management: Securely manage user sessions, using short session timeouts and invalidating sessions on logout.
- Dependency Management: Regularly audit and update third-party libraries and frameworks to patch known vulnerabilities. Vulnerabilities in supply chain components are a growing threat.
Adopting OWASP mobile security principles and embedding them into your development culture is a proactive defense against common exploits.
e. Enable Real-Time Threat Detection
Even with the best preventative measures, some threats may still slip through. Real-time threat detection acts as an early warning system, allowing for rapid response to evolving threats.
- AI/ML-Based Monitoring Tools: Leverage advanced AI and Machine Learning (ML) solutions to monitor app behavior, user activity, and network traffic for anomalies. These systems can learn normal behavioral patterns and quickly flag suspicious deviations (e.g., unusual login times, irregular API calls, unexpected data transfers).
- Behavioral Analytics: Implement User and Entity Behavior Analytics (UEBA) to identify abnormal activities that might indicate an insider threat or a sophisticated external attack.
- Automated Incident Response: AI-driven systems can automate initial incident responses, such as isolating suspicious sessions, alerting administrators, or triggering protective measures instantly, significantly reducing response times.
Threat detection in mobile apps powered by AI and ML provides a crucial, dynamic defense against sophisticated attacks that traditional signature-based systems might miss.
f. Use Cloud-Native Security Architecture
Most on-demand apps rely heavily on cloud infrastructure for scalability and resilience. Securing your cloud environment is non-negotiable.
- Secure Containers and Orchestration: If using containerization (Docker, Kubernetes), ensure containers are hardened, regularly scanned for vulnerabilities, and run with the principle of least privilege. Implement robust Kubernetes security practices.
- Cloud Identity and Access Management (IAM): Rigorously control who has access to your cloud resources and what actions they can perform. Implement Zero Trust principles: "never trust, always verify."
- Encryption Keys Management: Securely manage and rotate encryption keys using cloud-native key management services (KMS).
- Cloud DDoS Protection: Utilize the cloud provider's DDoS (Distributed Denial of Service) mitigation services to protect against volumetric attacks that can disrupt your service and expose vulnerabilities.
- Security Configuration Management: Continuously monitor and enforce secure configurations for all cloud services. Misconfigurations are a common cause of cloud-related breaches.
Prioritizing cloud security for mobile applications involves leveraging your cloud provider's security features and implementing best practices for your cloud-native architecture.
g. Ensure GDPR Compliance and Regional Privacy Laws
Beyond technical security, legal and ethical handling of user data is paramount. A data breach can lead to severe penalties under data protection regulations.
- GDPR (General Data Protection Regulation): For any on-demand app operating in or serving users in the European Union, strict GDPR compliance is mandatory. This includes explicit consent requirements, data minimization, data portability, the right to be forgotten, and strict data breach notification timelines (within 72 hours). Updates in 2025 emphasize expanded scope (e.g., biometric data), stricter consent rules, and increased penalties.
- CCPA/CPRA (California Consumer Privacy Act/California Privacy Rights Act): For apps operating in the USA, particularly California, understanding CCPA/CPRA is crucial. These laws grant consumers significant rights over their personal information.
- PIPEDA (Personal Information Protection and Electronic Documents Act): For Canadian operations, PIPEDA mandates how private sector organizations collect, use, and disclose personal information.
- Privacy by Design and Default: Integrate privacy considerations into the app's design and development from the outset, rather than as an afterthought.
- Data Mapping and Inventory: Understand exactly what data you collect, where it's stored, who has access, and for what purpose.
Ensuring GDPR compliance for apps and adherence to other regional privacy laws is critical not only for legal standing but also for building and maintaining user trust.
Checklist: 2025 App Security Essentials
Here's a quick checklist to help you verify your on-demand app's security posture:
- Enable MFA for all user and admin accounts
- Encrypt all data (TLS 1.3 in transit, AES-256 at rest)
- Use an API Gateway with rate limiting & strong authentication
- Follow OWASP Mobile Top 10 secure coding standards
- Run regular security audits & penetration tests
- Continuously train developers on security and threat trends
- Deploy AI/ML-based threat detection for real-time defense
- Harden your cloud setup with IAM, container & DDoS security
- Comply with GDPR, CCPA, PIPEDA and obtain user consent
- Maintain clear privacy policies
- Create and test an incident response plan
- Regularly patch and update all software components
Conclusion
In 2025, the digital battlefield is more complex than ever. For on-demand apps, where user trust is the ultimate currency, data security is not just a feature; it's a foundational pillar of business survival. Cybercrime is evolving at an alarming pace, making proactive and adaptive defense strategies mandatory. By diligently implementing these security tactics, you're not just preventing data breaches; you're building a resilient, trustworthy, and future-proof platform. Investing in robust security measures from day one protects your users, your reputation, and ultimately, your bottom line.
